This topic describes the basic concepts relevant to the VEN and for Illumio Core software. Additionally, it explains the VEN architecture and components.
Basic Concepts for Illumio Core Software
- A workload is bare metal server, virtual machine (VM), or a container.
- The VEN is a lightweight, multiple-process application with a minimal footprint that runs on a workload.
- Native network interfaces are also know as the OS's firewall platform.
The VEN manages firewalls at an OS level, so you must install a VEN on every bare-metal server or virtual machine you want to secure. However, you only need to install a single VEN to secure all the containers on a machine. A secured workload is known as a managed workload.
Once installed, the VEN performs the following tasks:
- Interacts with the native networking interfaces to collect traffic flow data.
- Enforces policy received from the PCE.
- Only consumes CPU as needed to calculate or optimize and apply the firewall, and so on, while remaining idle in the background as much as possible.
- Uses configurable operational modes to minimize the impact to workloads.
- Summarizes the collected traffic-flow data, then reports it to the PCE.
You control the VEN's operations through the PCE web console or from the command line on the machine with the installed VEN itself.
Activation or Pairing
The terms “activation” and “pairing” indicate the same function from different perspectives, namely putting the workload under managed control by the PCE:
- The VEN sees itself as activated or deactivated.
- The PCE sees a VEN as paired or unpaired.
Pairing and Activating the VEN
| 1 | The VEN is installed. | The PCE remains unaware the VEN is present. |
| 2 | The VEN and the PCE are paired. |
The PCE uses a pairing key (activation code) to pair with the VEN. After pairing, the PCE becomes aware of the VEN. |
| 3 | The VEN is activated. |
The VEN uses an activation code generated by the PCE. After activation, the VEN is ready to function. |
Unpairing or Deactivating the VEN
-
When the PCE is unpaired with the VEN, the VEN is deactivated and uninstalled.
-
When the VEN is deactivated, it remains installed and can be reactivated.
-
Use the illumio-ven-ctl command to deactivate the VEN. You can't deactivate a VEN by using the PCE UI; you may only unpair it.
VEN Architectural Diagram
At startup, the VEN instantiates the following processes or services.
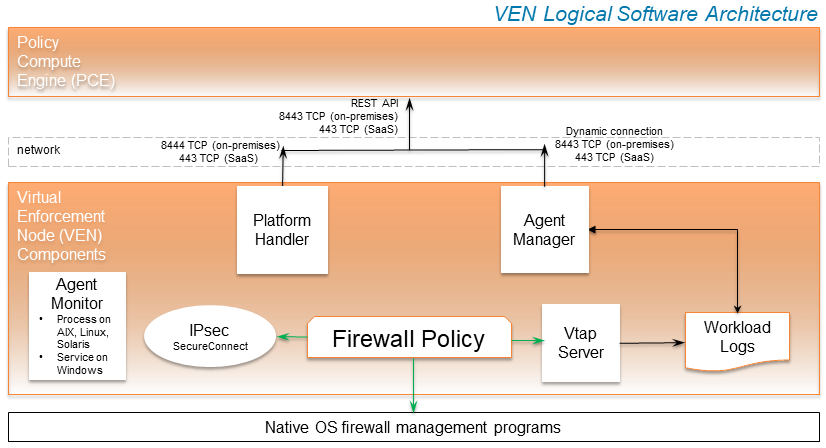
- The VEN reports to the PCE the status of the workloads.
- The PCE computes a unique security policy for each managed workload and transmits it to the VEN.
- The VEN receives the policy and it programs a firewall by using the firewall platform of the OS. The VEN supports the following firewall platforms:
- iptables (older Linux)
- Nftables (newer Linux)
- Packet Filter (newer Solaris)
- Ipfilter (older Solaris)
- Windows Filtering Platform (Windows)
- When the VEN is finished programming a firewall for each workload, it reports back to the PCE. The PCE then considers these workloads as having a synced policy.
Main Components of the VEN
|
VEN Process |
Description |
Linux/AIX/Solaris User |
Windows User |
|---|---|---|---|
|
AgentManager
|
|
root
|
LOCAL SYSTEM |
|
PlatformHandler
|
|
root
|
LOCAL SYSTEM |
|
VtapServer
|
|
|
LOCAL SERVICE |
|
AgentMonitor
|
|
|
LOCAL SYSTEM |
SecureConnect Architecture
Illumio's optional SecureConnect feature configures Internet Protocol Security (IPsec), a set of protocols to enforce security for IP networks. IPsec can be configured to use cryptography.
IPsec runs as root in LOCAL SYSTEM.
VEN Interactions with Files and Components
The VEN interacts with files and components for installation, root tasks, and initialization tasks. Minor tasks include working with install logs, the registry key, and read-only access to machine resources.
The VEN interacts with the following files and components:
Linux/AIX/Solaris
|
Function |
Description | File/Location |
|---|---|---|
| Root file | DATA_ROOT is a variable that points to a filepath. | /opt/illumio_ven_data (by default) |
| Package repository | INSTALL_ROOT is a variable that points to a filepath. | /opt/illumio_ven (by default) |
| System initialization | Initializes system | /etc/illumio_ven (typically) |
| Persistent install log | Persistent install log | /var/log/illumio.log
|
| Firewall | Dynamically addS IPs to ipsets: | Snoop on special packets. |
| Strongswan IPSec system. | Snoop on Security Associations. | |
| Read system files (e.g., netstat). | /proc
|
Windows
|
Function |
Description | File/Location |
|---|---|---|
| Runtime data files | DATAFOLDER is an installer parameter that points to a filepath. | c:\ProgramData\Illumio (by default) |
| Executable program files | INSTALLFOLDER is an installer parameter that points to a filepath. | c:\Program Files\Illumio (by default) |
| Install log | Persistent install log. |
|
| System initialization | N/A | N/A |
| Firewall | For network filtering. | Windows Filtering Platform |
Management Interfaces for the VEN and PCE
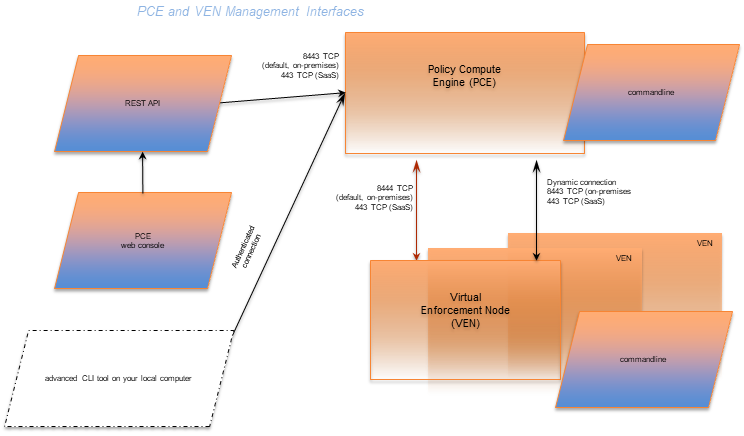
The diagram below is a logical view of the management interfaces to the PCE and VEN.
|
Interface |
Notes |
See... |
|---|---|---|
|
PCE web console |
With the PCE web console, you can perform many common tasks for managing Illumio Core. |
Security Policy Guide |
|
PCE command line |
Use of the command line directly on the PCE. A primary management tool on the PCE is the command line |
|
|
PCE advanced command-line tool |
From your own local computer, you can run the PCE advanced CLI tool for many management tasks on the PCE's resource objects:
|
|
|
REST API |
With the Illumio Core REST API, you can perform many common management tasks. One use is to automate the management of large groups of workloads, rather than each workload individually. The endpoint for REST API requests is the PCE itself, not the workload; the REST API does not communicate directly with the VEN. |
|
|
VEN command line |
A primary management tool on the VEN command line is the |