Load Balancers
By applying labels to your load balancer's virtual servers, you can write rules that allows client workloads in front of the load balancer to communicate with the virtual IP address of the load balancer's virtual servers. By adding labels to the pool members behind a virtual sever, you can allow communication from the load balancer to the members of the pool. The source for this communication is determined by the load balancer. The Illumio Core programs policies on the load balancer to enforce security policy. The PCE uses the load balancer's REST APIs to read and write security policies to configure security rules.
The PCE supports configuration of two load balancer units if they are configured in Active/Standby or Active/Active modes. The PCE needs to be configured with the user name and password of an administrative user who has read-write access to all configurations on the load balancer.
The PCE configures new objects on the load balancer and does not alter any existing configurations. When a created object in the load balancer configuration is modified, the PCE detects it as tampering and modifies the configuration back to the intended state so that the correct security policy is enforced.
The Illumio Core dynamically adjusts policies on the load balancer based on application and topology changes in the datacenter so that the Illumio Core can enforce consistent security policy on load balancers across the datacenter and cloud environments, as well as show the application traffic in Illumination. The Illumio Core keeps track of the policy it programmed and reconfigures policy if it was altered on the load balancer manually or by other means.
The Illumio Core makes use of the following constructs on load balancers:
• LTM: iRules on LTM provide capability to restrict application access. When LTM is used as enforcement mechanism, the Illumio Core uses virtual-server based iRules and Datagroup Lists.
- AFM: AFM provides stateful firewalling on BIG-IP. When AFM is used as an enforcement mechanism, the Illumio Core uses Network Firewall policies in the virtual server section and address-lists in the network firewall.
- AVI: The Illumio Core uses the Network Security Policy rules to program AVI Vantage.
Configuring two F5 units in Active/Standby mode is supported
F5 BIG-IP Requirements
The Illumio Core uses its REST API to program F5 load balancers, which means that F5 needs to be running a software version that supports REST-API. The requirements include:
- BIG-IP 11.5.x or higher
- Utilize SNAT or Auto-map mode
AVI Vantage Requirements
- AVI Vantage 18.2.3 or higher
Virtual Servers
Virtual servers in the Illumio Core contain two parts:
- A virtual IP address (VIP) and port through which the service is exposed
- Local IP address(es) used to communicate with backend servers (pool members).
A virtual server is similar to a workload. It can be assigned labels and has IP addresses, but does not report traffic to the Illumio Core. Each virtual server has only one VIP. The local IP addresses are used as a source IP address for connections to the pool members (backend servers) when the virtual server is operating in SNAT mode or Auto mode. These IP addresses are likely to be shared by multiple virtual servers on the server load balancer.
A virtual server is identified by a set of labels. The consumers and providers for a virtual server can be assigned different labels, which could place them in the same group or a different group in Illumination.
Providers are allowed to have an incomplete label set (for example, only a Location label), so the providers can be in all groups within the specified location. As a result, a single virtual server can have providers in any group or in any number of groups in Illumination.
Virtual Server Members
The Illumio Core allows you to write rules to allow communication with workloads managed by a load balancer using labels.
When you configure load balancers in the PCE, it connects to the load balancer using the Illumio Core REST API. The PCE reads all the load balancer virtual servers configurations and populates the Discovered Virtual Servers tab of a load balancer's details page. Any virtual servers associated with the load balancer can be converted to a managed virtual server for use with the PCE. When you configure the virtual server in the PCE web console, you can apply labels to the virtual servers. After configuring a virtual server, you can write a rule that allows other clients to communicate with it.
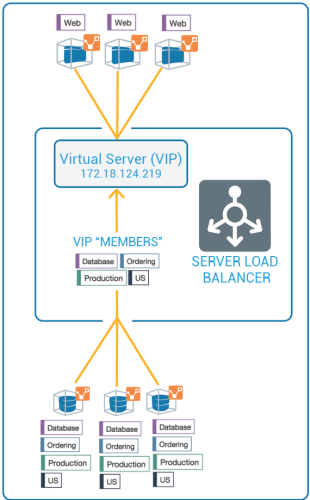
The members behind a virtual server are specified by configuring a set of labels in the virtual server configuration. A set of four Illumio labels can be applied on the Virtual Server Members tab, which is used to match the same set of labels on workloads in the virtual server's pool. If any of the workloads in the virtual server pool share the same set of four labels specified under the Virtual Server Members tab, then any rule you write with the virtual server also applies to the workload members.
In this diagram, you can see how the workloads that belong to the virtual server pool have the same labels specified on the Virtual Server Members tab:
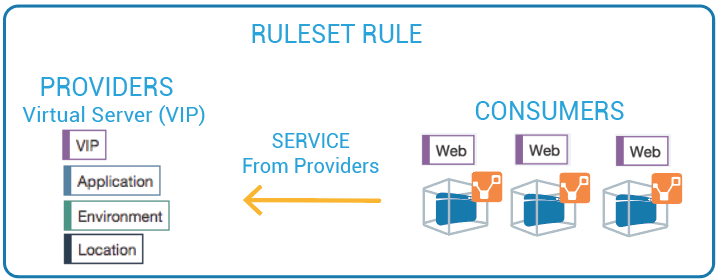
Ruleset Rule for Virtual Server
This diagram illustrates the rule you can write after you label a virtual server and its members:
Configure Virtual Servers
After adding a load balancer to the PCE, you can manage its virtual servers. For each virtual server, you can add a complete set of the four Illumio labels: Role, Application, Environment, and Location. Adding labels to the virtual server enables you to add it in a rule.
You add the four Illumio labels to the Virtual Server's Members tab. When the labels specified under Virtual Server Members match labels of workloads in the virtual server pool, any rule you write with the virtual server are applied to the workload members.
Configuring a load balancer's virtual servers consists of these three settings:
- Enforced or Not Enforced: When you select Enforced, any rules you write using the labels associated with the virtual servers and any of its members are enacted. Selecting Not Enforced disables the labels and any policy written that affects the virtual server or its members is disabled.
- Service: Select the service to use for the rules that allow access to the virtual server. For example, HTTPD 80 TCP.
- Labels: You must apply one each of the four Illumio labels to the virtual server: Role, Application, Environment, and Location. Assigning labels enables the virtual server to be used in rules.
Virtual Server Limitations
- Illumination does not support location-level and application-level maps.
- If a single SNAT pool is shared between multiple virtual servers, the Illumination map does not render correctly.
- SNAT and Auto-map modes of F5 virtual servers are supported. Transparent mode is not supported.
Virtual Server Methods and Parameters
Here are the methods to manage Virtual Servers.
| Functionality | HTTP and URI |
|---|---|
| Get a list of Discovered Virtual Servers | GET [api_version][org_href]/discovered_virtual_servers/:uuid
|
| Get a list of Virtual Servers | GET [api_version][org_href]/sec_policy/:version/virtual_servers
|
| Get a specified Virtual Server | GET [api_version][org_href]/sec_policy/:version/virtual_servers/:uuid
|
| Create a Virtual Server object | POST [api_version][org_href]/sec_policy/:version/virtual_servers
|
| Modify the enforcement mode, labels, and backend/provider labels of a specified Virtual Server | PUT [api_version][org_href]/sec_policy/:version/virtual_servers/:uuid
|
These are the parameters for Virtual Servers :
| Parameter | Description | Type |
|---|---|---|
name
|
The short friendly name of the virtual server | String |
labels
|
Label URI | String |
service
|
URI of associated service Service URI |
String |
providers
|
Includes Label and Workload information |
String |
mode
|
Management mode of the virtual server. |
String |
discovered_virtual_server
|
Corresponding discovered virtual server, server URI | String |
created_at |
The time (rfc3339 timestamp) at which this virtual server was created | date-time |
updated_at
|
The time (rfc3339 timestamp) at which this virtual server was last updated |
|
created_by
|
The URI of the user who created this virtual server | String |
updated_by
|
The URI of the user who last updated this virtual server | String |