This section describes how to manage workload by using the Workload pages in the PCE web console.
Overview of Workload Attributes
Workloads have the following attributes:
- Workload enforcement and visibility state
- Connectivity and policy sync state
- Workload labels
- Attributes
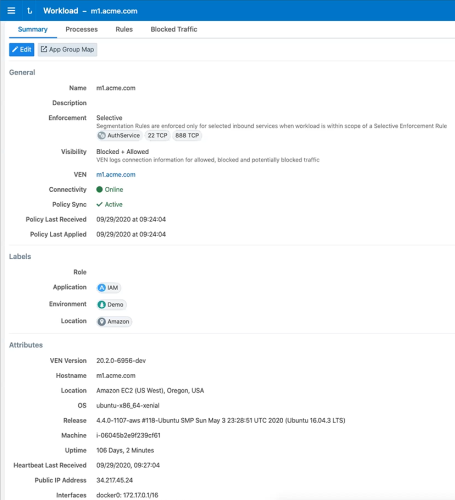
Workload Summary
The workload summary displays information about the workload, including the user-specified attributes at the time of pairing and information that the Illumio Core has automatically detected about the workload, specifically:
- The name of the workload
- A description (if provided)
- The Workload Enforcement States
- The visibility the VEN uses
- The dates when the policy was revised and last applied
- The workload's VEN connectivity status; see VEN-to-PCE Communication in the VEN Administration Guide
- The workload's VEN policy sync status; see VEN Policy Sync in the VEN Administration Guide
- Any labels applied to the workload
- Workload system attributes (such as VEN version number, hostname, and uptime)
Workload Processes
In the Workload Processes tab of the Workload detail page, you can view the processes currently running on the workload.
For each process running on the workload, the following information is listed:
- Process name
- Server path
- Ports used by the process
- Protocol (for example, TCP or UDP)
To organize the listed items, you can select the column headings to sort the processes by that attribute. For example, when you click the Protocol column heading, the processes are grouped by protocol so that all processes using UDP are listed together and all processes using TCP are listed together.
On the Workload Processes tab, when you delete the binary for that process while the process is running, the PCE appends the process name with “(deleted).”
The UDP - PCE UI processes tab shows both server and client UDP processes and ports.
On the Services tab for a workload, both UDP client and server processes show up along with their port numbers. For TCP, only listening ports/processes are presented.
For UDP, only listening ports/processes should be presented. The information is coming from service-reports sent by VEN once every 24 hours.
Customers depend on this information to understand the provider-processes in their datacenter and write policies to allow traffic from needed workloads.
Policy state determines how the rules affect a workload's network communication. The Illumio Core includes four policy states for workloads. If a workload is unmanaged, the Policy State column is not displayed on the workload list page.
Idle
The Idle state is used for installing and activating VENs on workloads without changing the workloads' firewalls. In the Idle state, the VEN on the workload does not take control of the workload’s iptables (Linux) or Windows firewall (Windows), but uses workload network analysis to provides relevant details about the workload to the PCE, such as the workload’s IP address, operating system, and traffic flows. This snapshot is taken every 10 minutes.
A pairing profile can be used to pair workloads in the idle state.
SecureConnect (IPv6 compatibility) is not supported on workloads in the Idle state. When you activate SecureConnect for a rule that applies to workloads that are in both Idle and Non-idle policy states, it can impact the traffic between these workloads.
Visibility Only
In the Visibility Only state, the VEN inspects all open ports on a workload and reports the flow of traffic between it and other workloads to the PCE. In this state, the PCE displays the flow of traffic to and from the workload, providing insight into the datacenter and the applications running in it. No traffic is blocked in this state. This state is useful when firewall policies are not yet known. This state can be used for discovering the application traffic flows in the organization and then generating a security policy that governs required communication.
Selective Enforcement
Segmentation rules are enforced only for selected inbound services when a workload is within the scope of a Selective Enforcement Rule.
Full Enforcement
Segmentation Rules are enforced for all inbound and outbound services. Traffic that is not allowed by a Segmentation Rule is blocked.
Visibility Level
You can choose from three levels of visibility for workloads. These modes allow you to specify how much data the VEN collects from a workload when in the Full Enforcement state:
-
Off: The VEN does not collect any information about traffic connections. This option provides no Illumination detail and demands the least amount of system resources from a workload.
This property is only available for workloads that are in the Full Enforcement state.
- Blocked: The VEN only collects the blocked connection details (source IP, destination IP, protocol and source port and destination port), including all packets that were dropped. This option provides less Illumination detail but also demands fewer system resources from a workload than high detail.
- Blocked + Allowed: The VEN collects connection details (source IP, destination IP, protocol and source port and destination port). This applies to both allowed and blocked connections. This option provides rich Illumination detail but requires some system resources from a workload.
Workload Rules
In the Rules tab of the Workload detail page, you can view the rules that are currently applied to the workload. The Illumio Core has two types of rules:
- Inbound Rules: Show all the services on the workload and the endpoints that are allowed to communicate with these services.
- Outbound Rules: Show all the endpoints the services on that workload that are allowed to communicate with.
To apply rules to a workload, create a segmentation ruleset and then make sure that the ruleset and workloads share the same labels. See Create a Segmentation Ruleset for information.
The workload rules are listed against individual IP addresses in an ipset. The PCE places a limit on the size of the returned data. The PCE web console displays an error message whenever the PCE exceeds a certain number of rules and that count is the number of peer-to-peer rules calculated for that workload.
Workloads Blocked Traffic
The Blocked Traffic tab shows you all traffic that attempted to communicate with your workload but was blocked due to policy. For information, see Blocked Traffic.
Filter the Workloads List
You can filter by one or any combination of workload labels and properties. For example, you can use the Workload filters to see only workloads that have the Role label named Web, that are running Linux Ubuntu, that are in the Visibility Only state, with a VEN policy sync status of Active, that have a specific IP address, and that have “asset” in the hostname.
-
Use the filter at the top of the Workloads and VENs page to do a label-based search. For example, you can filter the list to view all workloads that have the Application label “Application12345.”
-
You can filter workloads based on their properties, such as workload name, IP address, description, hostname, OS family, VEN connectivity, and when a policy was last applied to or received by the workload, and when was the last heartbeat received.
Click the Refresh button to refresh the content of the page with the latest information without clearing the filters or the results.
Use a Wildcard to Filter Workloads
To help sort and organize large numbers of workloads, the Workloads filter supports a wildcard character for the Name and Hostname properties.
To filter the list of workloads on the Workloads page, select either the Name or Hostname property from the drop-down list and enter the search terms using the asterisk ( * ) character as a wildcard. The asterisk can represent any number of characters.
For example, you can enter “db-*auto” using the Name property to find workloads with names that include “db,” “-auto,” and any number of characters in between (for example, “db-prod-auto,” “db-dev-auto,” or “db-12-auto”).
At least one non-wildcard character must be included before or after the wildcard character. An error message is displayed when you include only the wildcard character in the search field.
The auto-complete feature is disabled when the wildcard character is used.
Use Clone Alerts to Filter Workloads
Workloads can be filtered according to whether a clone has been detected. If the are are any workloads that are in the clone detected state, a red banner (similar to workloads in suspension) is displayed at the top of the workload list page.
The VEN communicates with the PCE using HTTPS over Transport Layer Security (TLS). Additionally, a clone token is generated. When an agent token is mistakenly or maliciously reused on another workload, the clone token is used to detect the condition and disambiguate the hosts. The clone token is periodically rotated. The agent token is never rotated.
To filter by clone alerts:
- In the PCE web console, display the Workloads List page.
- Look for an alert banner indicating some workloads are in "clone detected" state. This banner will appear only if, for example, you pair one or more VENs and then clone the VEN(s).
- Click the filter link on the banner. The list now shows only the "clone detected" workloads.
- Click on one of the "clone detected" workloads. An alert is displayed on the detail page for that workload.
- If you stop, unpair, or repair the cloned VEN, you can come back and see that the messages and alerts are removed from the Workloads List page.
Enforce a Workload Policy State
- From the PCE web console menu, choose Workloads and VENs > Workloads.
- Select the workload that you want to change the Enforcement state..
-
From the Enforcement drop-down list, select Idle, Visibility Only, Selective, or Full depending on how you want to allow or block traffic connections.
A dialog box appears directing you to confirm your change.
- Click OK.
Set Workload Interfaces to Ignored
You can set interfaces from being Managed to Ignored in the PCE web console. You can use this option when you want the workload to ignore visibility and enforcement on the interconnected interfaces of database clusters such as, Oracle RAC. During pairing, you can set one or more interfaces to Ignored, which causes the first downloaded firewall to ignore those interfaces. After you set an interface to Ignored, that interface is not be included in the policy configuration and traffic flows uninterrupted through it without any change in latency. You can see which interfaces are marked as Ignored on the Workloads’ Summary page.
- From the PCE web console menu, choose Workloads and VENs > Workloads.
- Click a workload to open the details.
- Click Edit.
-
In the Network Interfaces section, change interfaces from Managed to Ignored using the PCE Action drop-down list.
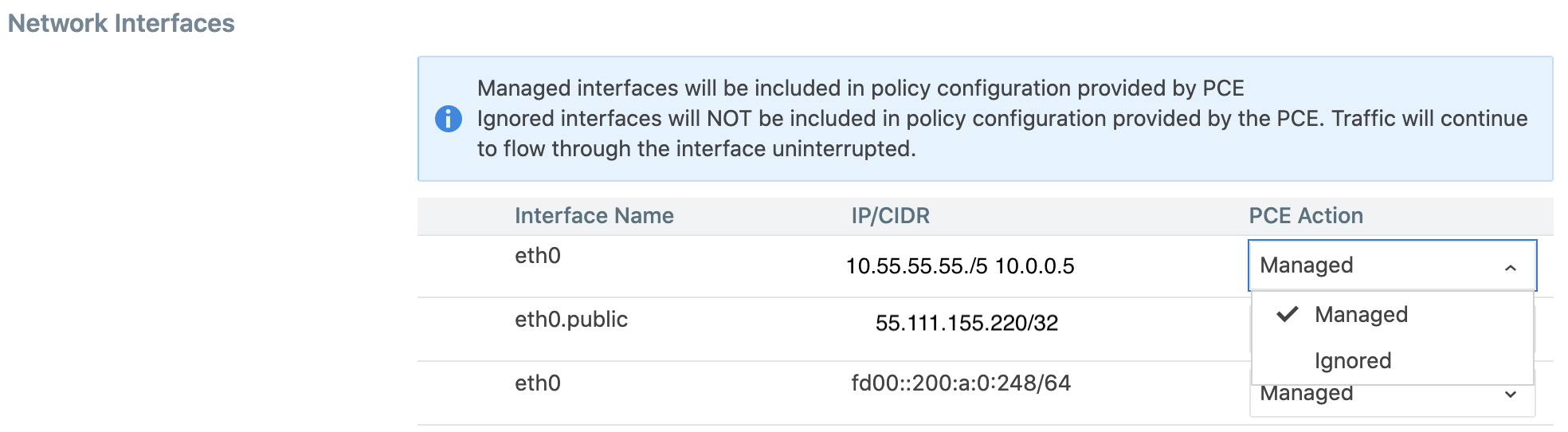
In case you are editing an unmanaged workload, you will not have the option to ignore the workload using the PCE Action drop-down. That drop-down menu does not exist for unmanaged workloads. You can still provide information on the Interface Name and the IP/CIDR address.
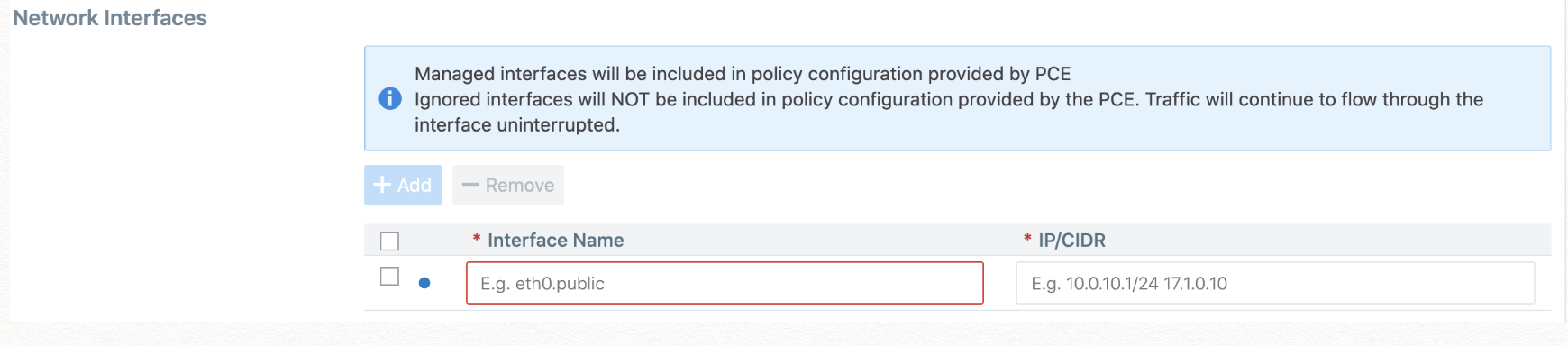
- Click Save.