The PCE enforces password policies that only a Global Organization Owner can configure. In the PCE web console, you set password policies that the PCE enforces, such as password length, composition (required number and types of characters), and password expiration, re-use, and history.
About Password Policy for the PCE
You need to be a Global Organization Owner to view the Password Policy feature under the Access Management> Authentication menu options.
Organizations using SAML authentication can not use the PCE's Password Policy features to configure password policies. The PCE enforces the password policy only for local users created in the PCE. For users who authenticate to the PCE using SAML authentication, the PCE relies on the SAML Identity Provider to enforce the password policy. The PCE does not store the passwords for such external users. Hence, any password policy enforcement must be configured in the SAML Identity Provider.
Permission to edit this setting is dependent on your role. See About Roles, Scopes, and Granted Access for information.
Password Requirements
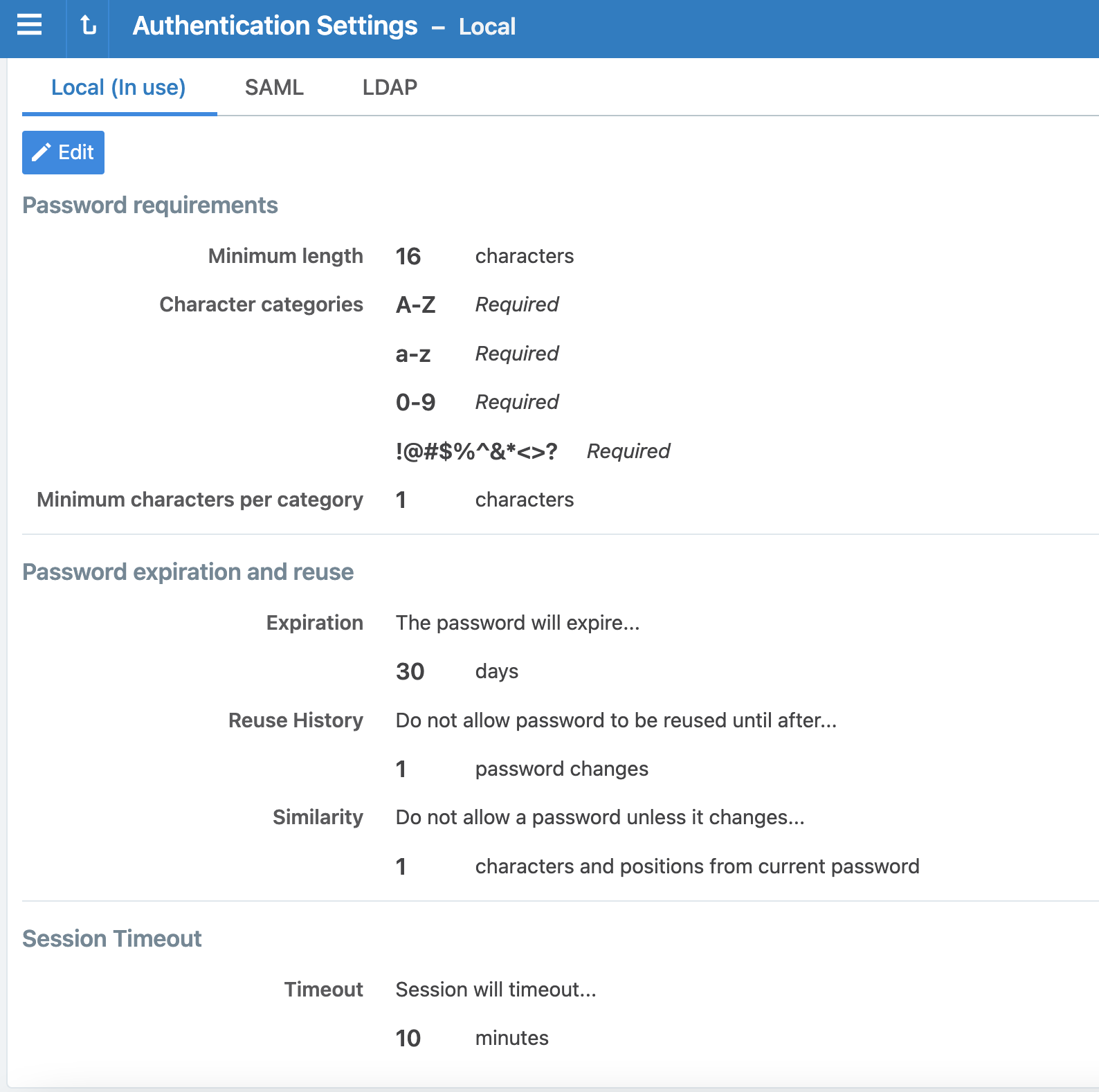
The password requirements you set are displayed to users when they are required to change their passwords. You can set the minimum character length, ranging from a minimum of 16 characters to a maximum of 64 characters. The default length is 16 characters.
A Global Organization Owner should configure passwords based on the following categories:
- Uppercase English letters
- Lowercase English letters
- Numbers 0 through 9 inclusive
- Any of the following special characters:
! @ # $ % ^ & * < > ?
You have to select at least three of the above categories. The default password requirement is one number, one uppercase character, and one lowercase character. You can set the password to use either one or two characters from each category.
Password Expiration and Reuse
You can set the password expiration range from 1 day to 999 days. The default setting for password expiration is “Never.”
You can set the password reuse history from 1 to 24 passwords before a user can reuse the old password. The default setting is five password changes before reuse of the password is allowed.
The number of password changes before password reuse is allowed is the value you enter + 1 (the current password). For example, when you specify 3, the number of passwords before reuse is allowed is 4.
You can also set the similarity of a password by not allowing a user to change their password unless it changes from a minimum of 1 to a maximum of 4 characters and positions from their current password.
Allowable password reuse and password history can be set to from 1 to 24 passwords before reuse is allowed. The default setting for password reuse is five password changes before reuse is permitted.
Caveats
- When a Global Organization Owner increases the required minimum password length policy or increases the password complexity requirements and enables the password expiration (1-999 days), all the existing users must reset their passwords based on the new policy.
- When a Global Organization Owner configures the password to never expire, all users who were migrated from an older release must reset their passwords when they next log in.
Change Password Policy Settings
- From the PCE web console menu, choose Access Management > Authentication.
- Click Configure (Local).
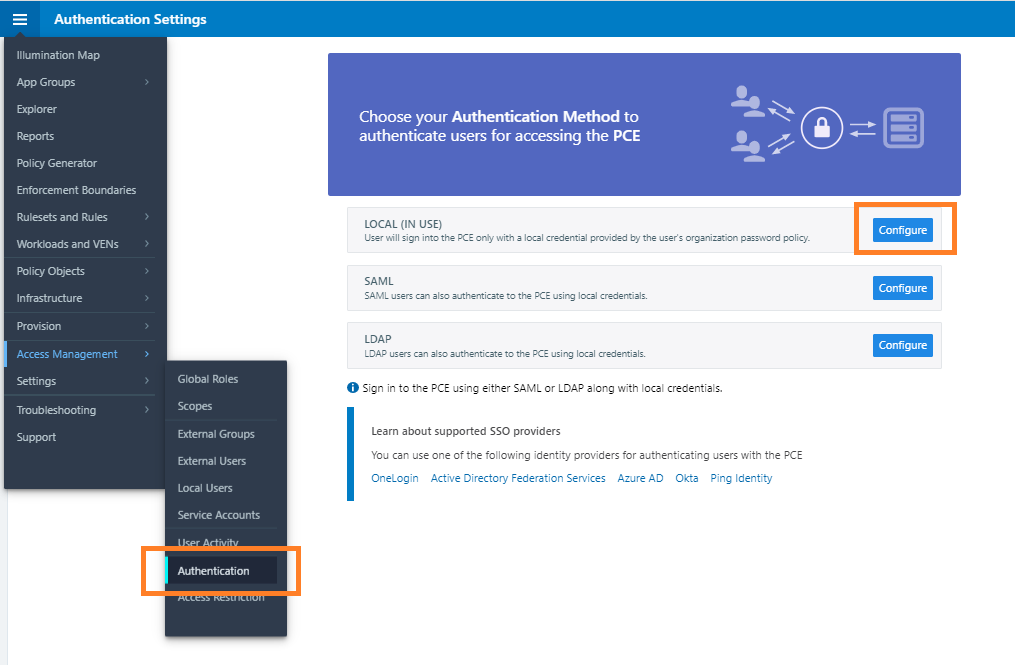
- Click Edit.
-
Configure the password policy for your Illumio Core users:
-
Click Confirm and then Save to save the password policy for your local users.
Configure Session Timeout
You can configure the session timeout value using the PCE web console. The session expiration timeout values must be set accordingly to balance security and usability so that your users can comfortably complete operations within the PCE web console without their session frequently expiring. The timeout value is dependent on how critical the application and its data are. For example, you might set the timeout to 3-5 minutes for high-value applications and 15-30 minutes for low-risk applications.
- From the PCE web console menu, choose Access Management > Authentication.
- Click Configure (Local).
- Click Edit.
-
In the Session Timeout section, set a value between 3 minutes and 30 minutes. By default, the value is 10 minutes.
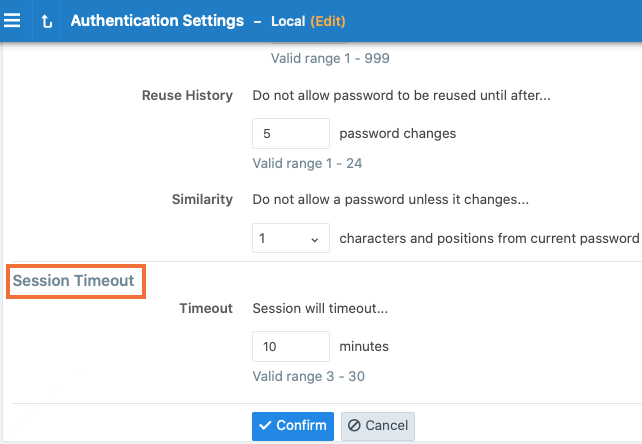
-
Click Confirm and then Save.
NOTE:The changed session timeout value applies to new browser sessions. Existing browser sessions are not affected when the session timeout value is changed.