Rules can allow or deny communication between multiple applications or entities. To write a rule, you need to define a source and a destination.
About Rules
Illumio Xpress supports the delegation of rule writing using role-based access control (RBAC). Application administrators can only edit rules where they have administrator privileges.
Rules allow the application administrator to write rules that allow other applications to communicate with the applications that they manage without requiring global administrator privileges. This feature allows users to group rules required for inter-application and intra-application communication for a specific application into one ruleset.
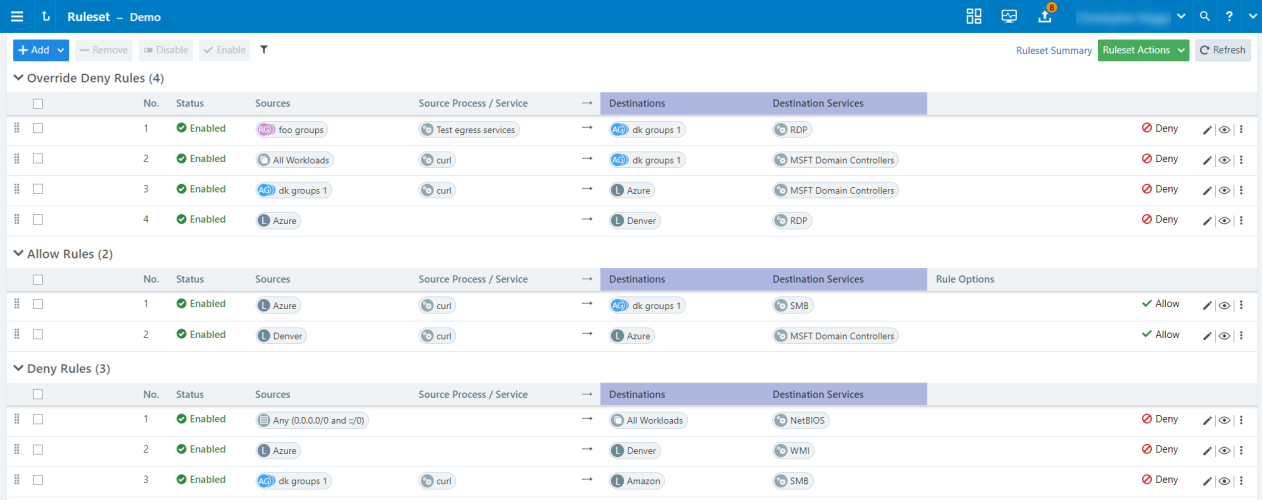
You can combine multiple types of rules (Override Deny, Allow, Deny) in a single ruleset.
You can use multiple services or ports and protocols in a rule. This approach helps reduce the number of rules in your PCEs, which helps improve the PCE performance.
Rule examples:
On the left-hand side, drag handles let you move each rule within its rule type for better organization. On the right-hand side, selectable icons let you edit the rule or see the rule's impact (affected traffic and overlapping rules). The vertical breadcrumb menu allows you to disable, duplicate, remove, or reverse a rule.
Override Deny Rules
These rules allow you to write rules that deny communication between sources and destinations. This rule type is typically used to deny communication between workloads that may inadvertently be given allow rules by another administrator. Override Deny rules take precedence over all other types of rules. Note that PCE-essential communications will still be allowed
Allow Rules
Allow rules allow authorized users to write rules that allow communication between applications. Specifically, you can write rules that allow Destination Workloads and services to accept connections from source Workloads and services. Non-corporate joined endpoints are now supported for Allow rules and can be configured in the rule options.
Deny Rules
Deny rules allow authorized users to write rules that deny communication between applications. Specifically, you can write rules that deny Destination Workloads and services from accepting connections from source Workloads and services.
Permitted Rule Writing Combinations
The following table explains the valid rule combinations between providers and consumers.
| If Destination is | And Service is | Source can be |
|---|---|---|
| Workload*, All workloads, label, label group | Any service | Workload , IP list (including Any (0.0.0.0/0 and ::/0), label, label group, user groups, All workloads |
| IP list | Any service | Workload, label, label group, user groups, All workloads |
| Uses virtual services and workloads | Any service |
Workload, label, label group, IP lists, All workloads, uses virtual service, uses virtual services and workloads |
| Workload, All workloads, label, or label groups | Any service |
User groups and one or more of the following: workload, All workloads, label, label groups |
* Deny and Override Deny rules do not allow workloads, but do allow "All Workloads."
Notice from the table that you cannot have rules governing traffic from one IP list to another IP list.
Be aware that if you do not specify a label for a specific dimension (e.g., Role, Application, Environment, Location), then the label will default to “All”
Stateless Rules
By default, all rules you write in the PCE are stateful, which means that the host's firewall keeps track of a connection for the entire duration of the session.
For Linux workloads, you can specify stateless packet filtering for a rule (“stateless”: true). This means that the VEN instructs the host's firewall to not maintain persistent connections for all sessions. You can create this type of a stateless rule for data center core services, such as DNS and NTP.
If you add a stateless rule to a policy that has both Windows and Linux workloads, then that rule is configured as a stateful rule on the Windows workload.
Caveats
In a stateless rule, you can add the following policy objects as consumers:
- An individual workload
- A label (one each of a specific type, up to four total)
- Any IP list plus All workloads
If you attempt to add any other consumers, you receive an error.
The Illumio Xpress limits the number of stateless rules to 100, to ensure that both stateful and stateless rules coexist on the host in a way that optimizes system and network performance. If you need more than 100 stateless rules in your Illumio Xpress policy, contact your Illumio Xpress Professional Services Representative for more information.
Existing active connections on workloads allowed by a stateless rule (for example, an SSH session) are terminated when workloads receive new rules from the PCE. Those connections need to be reestablished by the clients. For this reason, Illumio recommends that you use stateless rules for services that use high-frequency short-lived connections, such as DNS and SNMP.
Rule Search
When you have a large number of rules organized in rulesets, you can't easily search for rules across rulesets. Segmentation rule search solves this issue by making it simple to search for specific rules.
For example, when you want to know how many rules there are for SNMP (UDP 161) and you have around 200,000 rules organized across 700 rulesets, it is time-consuming to narrow down that search without using this feature.
You can search for and analyze rules that allow communication over a specific port and protocol.
- Segmentation Rule Search allows you to quickly find rules that apply to a set of providers and consumers.
- Providers and consumers can be represented by a workload, an IP address, or a set of labels.
- Using this feature helps you identify rules that are getting applied to your workloads due to unnecessarily broadly applicable rulesets or human errors.
To search for rules:
-
From the PCE web console main menu, choose Rulesets and Rules > Rule Search.
The Rule Search page appears.
- Search for Active or Draft rules.
- Perform a Basic or Advanced search of your rules:
- Basic: Searches all attributes
Advanced: Searches by provider, consumer, or both.
NOTE:When you perform an advanced search by workload name, the search results do not display the IP list rules when the iplist contains workload IP addresses because the Illumio Xpress does not resolve CIDRs and ranges within an IP list.
- From the Results drop-down list, choose to either have the exact match of the selected search filters to be displayed or a match to any of the selected filters (All Results).
- Click the Column drop-down list to select the attributes you want to be displayed in the search results.
- Filter options to further narrow your search.
- Under the Ruleset column, select a ruleset and make changes to the rules.
-
Click Download to download the results of your search.
You can download up to 500 rules in the CSV format.
Policy Check
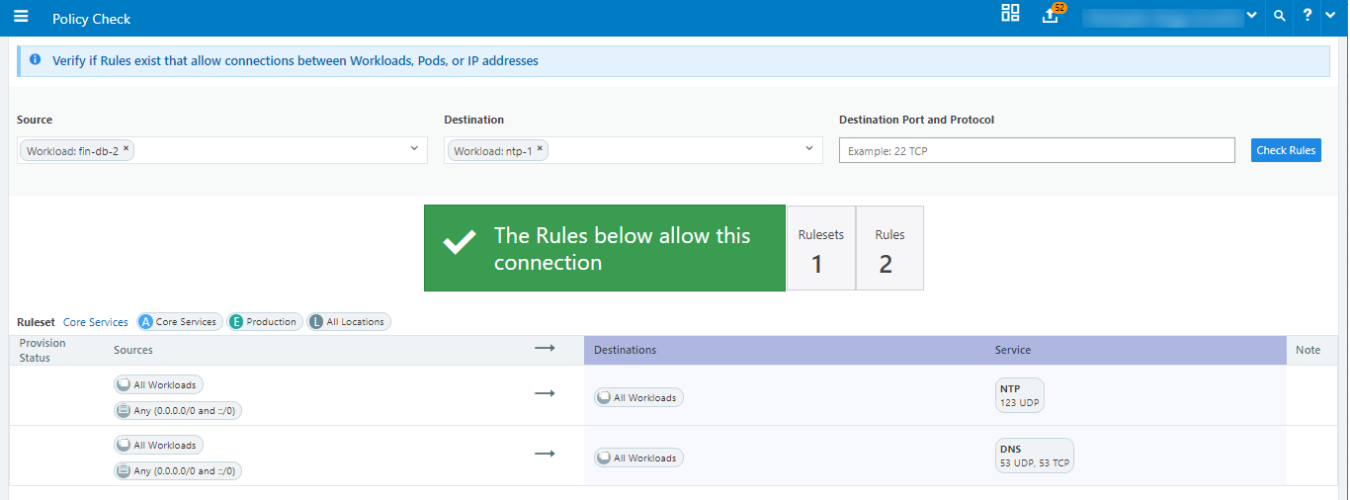
The Policy Check feature allows you to determine if a rule allowing communication between workloads or a workload and another IP address already exists. On the Policy Check page, you select two workloads or IP addresses to determine if a rule exists to allow communication between them.
You can do a policy check between two workloads, or a single workload and single IP address.
For example, you have created several rulesets for your workloads and applications and you want to know whether your organization has an existing rule for that traffic before you start writing new rules that duplicate those existing rules.
To perform a policy check:
- From the PCE web console main menu, choose Troubleshooting > Policy Check.
- In the Source field, type or select a workload or IP address.
- In the Destination field, type or select a workload or IP address.
- In the Destination Port and Protocol field, enter a port and protocol when the connection is running over TCP or UDP, or just a protocol when the connection is running over GRE or IPIP.
-
Click Check Rules.
If a connection is allowed between the selected two workloads or IP addresses, the page will display at least one rule that allows the connection.
-
NOTE:
The status column does not display any values. For more information, you can do a detailed search using the Rule Search feature.
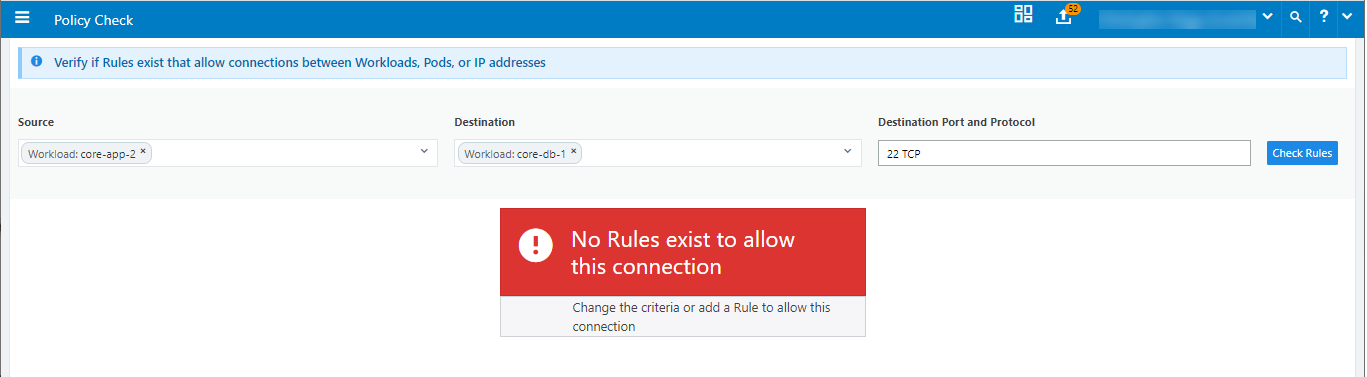
When a rule does not exists, the page displays the message “No Rules exist to allow this connection.”