You can install the VEN two ways. These two ways are nearly identical and achieve the same goal: VEN installation and upgrade.
- Using the VEN Library integrated into the PCE: This method is documented in the topics about installing and upgrading the VEN Library.
- Manual VEN installation on individual workloads with your own software deployment tools: This method is documented in the topics about installing and upgrading the VEN using the VEN CTL.
VEN Installation Using the VEN Library
The VEN Library installation and upgrade feature in the PCE is available for the RPM, Debian, and Windows distributions of the VEN software. Other workload operating systems are not supported.
Using the VEN Library in the PCE to install the VEN is a more automated approach than installing the VEN CTL but it gives you less control over optional aspects of VEN installation and upgrade.
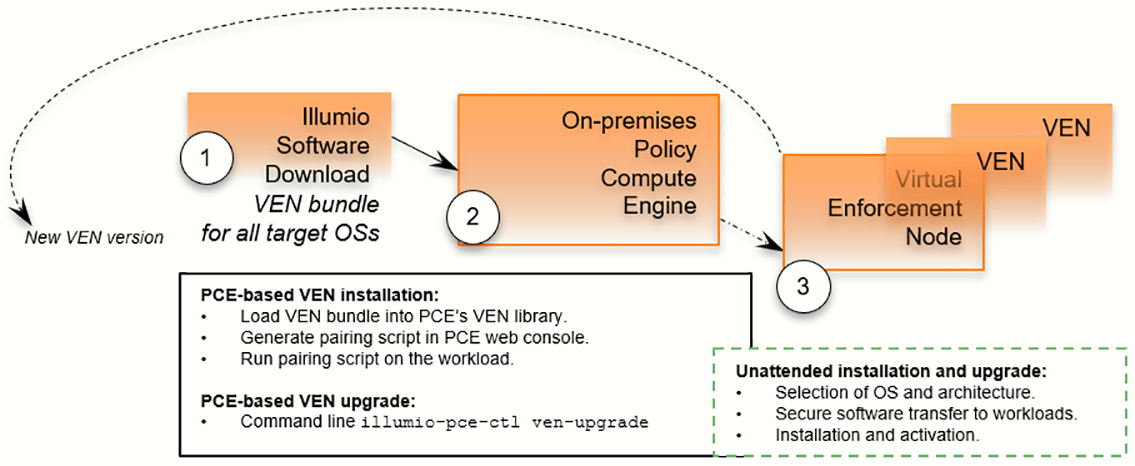
The VEN Library method of installation utilizes a VEN software bundle. A VEN software bundle is a collection of a particular VEN software version for all supported workload operating systems.
- In the PCE, you load a VEN software bundle into the VEN library. The VEN library is a collection of all VEN software versions you have loaded.
- For VEN installation:
- In the PCE web console, you set a default VEN version.
- In the PCE web console, you generate a pairing script to install and activate the VEN on target workloads.
- You copy the pairing script to the target workload and run it.
- The pairing script:
- Determines the OS and CPU architecture of the target workload.
- Securely transfers the VEN software to the target workloads.
- Installs the VEN software.
- Pairs the VEN with its PCE.
- For VEN upgrade, use the VEN Library in the PCE to upgrade all workloads or selective workloads.
- Some features are not available with VEN Library method, such as Kerberos-based authentication and custom settings with environment variables.
Illumio Xpress Operations sets up the VEN Library in the PCE for Illumio Xpress customers.
VEN Installation Using the VEN CTL
This method gives you greater control over optional aspects of VEN installation, pairing, and upgrade.
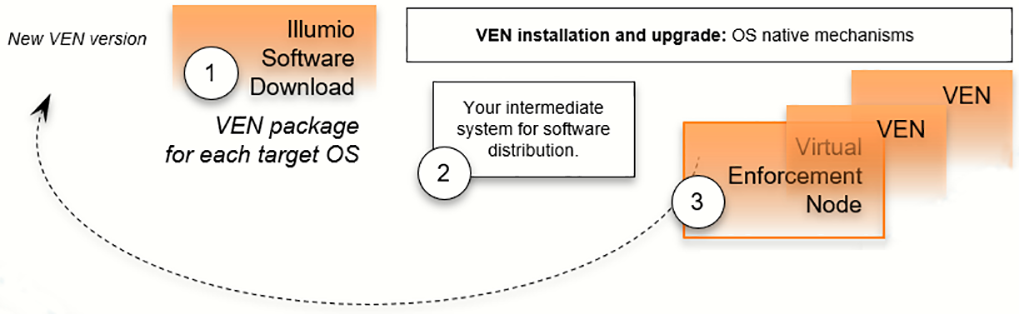
The VEN installation method using the CTL starts with downloading a VEN package. A VEN package is the VEN software for a single supported workload OS and CPU architectures. Installation and upgrade rely on package managers, which are standard, native OS tools.
- For VEN installation with this method:
- Determine the OS and CPU architecture of the target workloads.
Download the appropriate VEN packages.
For example, installing a VEN on CentOS 8 x86-64 requires you to download the VEN package
illumio-ven-XXX.c8.x86_64.rpm.NOTE:You are responsible for securely transferring the VEN software to the target workload with your own software deployment mechanisms.
- Optionally, set the following environment variables or command-line options:
- Custom installation directories
- Custom user and group names
- Kerberos-based authentication for VEN-to-PCE communications
Run the native OS installation mechanism.
For example:
rpm -ihv illumio-ven*.rpm- Pair the VEN with its PCE.
- You can pair the VEN during installation or after installation using the VEN CTL activate command (
illumio-ven-ctl activate <options>) - You can use a “prepare script” to install the VEN software on machine images and activate it at the next boot.
- You can pair the VEN during installation or after installation using the VEN CTL activate command (
-
If you installed the VEN with the VEN CTL and packaging CLI and customized installation options (such as, a custom installation directory or alternate VEN user), you cannot later upgrade the VEN by using the VEN Library in the PCE. You must upgrade the VEN using the workload's OS package upgrade process.
TIP:
If you try to upgrade a VEN using the VEN Library in the PCE but nothing happens, verify whether the VEN was installed by using the VEN CTL.
When to Use Which Method
You can use both methods at different stages of your VEN installation.
| Installation Method | Use Cases |
|---|---|
| VEN Library in the PCE |
|
| VEN CTL | To obtain more control over VEN installation and upgrade with a proprietary software distribution method |
VEN-to-PCE Authentication
Illumio Xpress has the following mechanisms for authentication between the VEN and the PCE:
- VEN pairing with the PCE
- Kerberos authentication with the PCE
Use one or both mechanisms across your organization, but they are mutually exclusive for the same workload.
This guide assumes that you already have a functional Kerberos service with which to authenticate.
VEN Authentication by Pairing with PCE
This is the default mechanism. When you install a VEN on a workload, the VEN is activated with an activation code generated by the PCE. The activation code is an identifier passed to the VEN software at activation.
After the VEN is activated, it communicates with the PCE over a secure connection. This process of activating a VEN is referred to as pairing it with the PCE. The term activation also applies when installing the VEN package directly on a workload by using the VEN CTL.
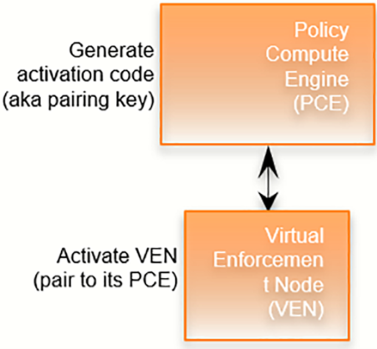
About the VEN Activation Code
The activation code is an identifier passed to the VEN software at activation. It is obtained from the pairing key. An activation code can be created for one-time use for a single workload or multiple uses for many workloads.
In the PCE web console, create a pairing profile. In the profile, you can specify one-time use or unlimited use for the activation code.
Activation Details
An activation code is used only after initially installing the VEN. During activation, the PCE generates an agent token. The VEN stores the agent token in a local file on the workload. The PCE stores the hash of the agent token. The VEN uses the agent token to uniquely authenticate itself to PCE. Only the agent token is used in VEN-to-PCE communication from that point on.
The VEN communicates with the PCE using HTTPS over Transport Layer Security (TLS) for REST calls and TCP over TLs for the events channel. Additionally, a clone token is generated. When an agent token is mistakenly or maliciously reused on another workload, the clone token is used to detect the condition and disambiguate the hosts. The clone token is periodically rotated. The agent token is never rotated.
VEN Authentication via Kerberos
You can configure the PCE and VEN to rely on authentication by a pre-configured Kerberos-based system, such as Microsoft Active Directory.
Kerberos-based authentication is supported when you install the VEN by using the VEN CTL. It is not supported when you use the VEN Library in the PCE to install the VEN.
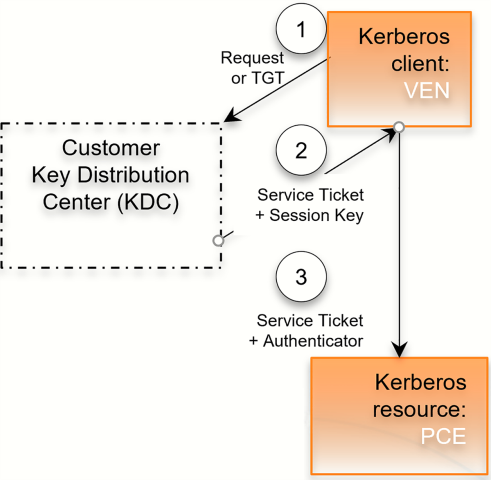
The Key Distribution Center (KDC) is your pre-configured Kerberos service; the VEN is a Kerberos client; and the PCE is a Kerberos resource.
- The VEN requests a session key or passes its ticket granting ticket (TGT).
- The KDC returns a service ticket and session key.
- The VEN passes the authenticated service ticket to the Kerberos-protected PCE.
For information about pairing workloads via Kerberos for each operating system, see the following topics:
VEN-unactivated Golden Masters
When you create machine images for faster deployment of the VEN, consider preparing them to pair the VEN with the PCE the first time the workload is booted. See Prepare Golden Image for Workload Installationfor information.