When workloads are paired with the PCE, the VEN discovers all running processes and services on a workload and makes those services available for use when writing rules. You can see those discovered services when you view the Processes tab on the Workload's details page.
To save new customers the chore of manually adding services, Illumio now pre-populates the Illumio Xpress instance with dozens of common services with their ports and protocols. These services are available in Main Menu > Policy Objects > Services. The pre-populated services are available in the appropriate dropdown menus when you create your rules.
However, you can also create your own to services to specify the service type, as well as the ports and protocols the services use to communicate.
Service names can be unrestricted, for example, sc.exe qsidtype myservice. You can write rules with unrestricted service IDs (SIDs). When there is a restricted SID, you should write rules without the SID. Including the service with a restricted SID type causes the traffic to be dropped and might cause traffic between the Reported view and Draft view to be reported inaccurately.
Service Types
When you create a service, you can choose one of two general types:
- All OS: Port Based: This type of service can be used for writing rules for any workloads and is defined by specifying a port and protocol, a port range, or in some cases, only the protocol. For example:
80 TCP,1000-2000 TCP,500 UDP. For GRE or IPIP, you only need to specify the protocol. -
Windows: Process/Service-Based: This type of service can be used for writing rules for Windows Workloads only and is defined by specifying one of the following combinations or scenarios. The Windows Process Path and the Windows Service Name must be surrounded by quotation marks:
-
Port and/or Protocol, Windows Process, and Windows Service
443 TCP c:\windows\myprocess.exe myservice -
Port and/or Protocol and Windows Process
443 TCP c:\windows\myprocess.exe -
Port and/or Protocol and Windows Service
443 TCP myservice -
Windows Port and/or Protocol
514 UDP -
Windows Process
c:\windows\myprocess.exe -
Windows Service
myservice
-
-
Windows Outbound: Process/Service-Based: This type of service can be used for writing rules for Windows Workloads only, like those above, except that they must be outbound, such as
c:\Windows\System32\dllhost.exe, for example. Source process enforcement requires a Window outbound service.
Create a Service
When you create a service, that service becomes available to use in a rule.
For a list of the types of services you can create, see Service Types.
Create a Typical Service
To create a service from the Services page:
-
From the PCE web console main menu, choose Policy Objects > Services.
-
Click Add.
-
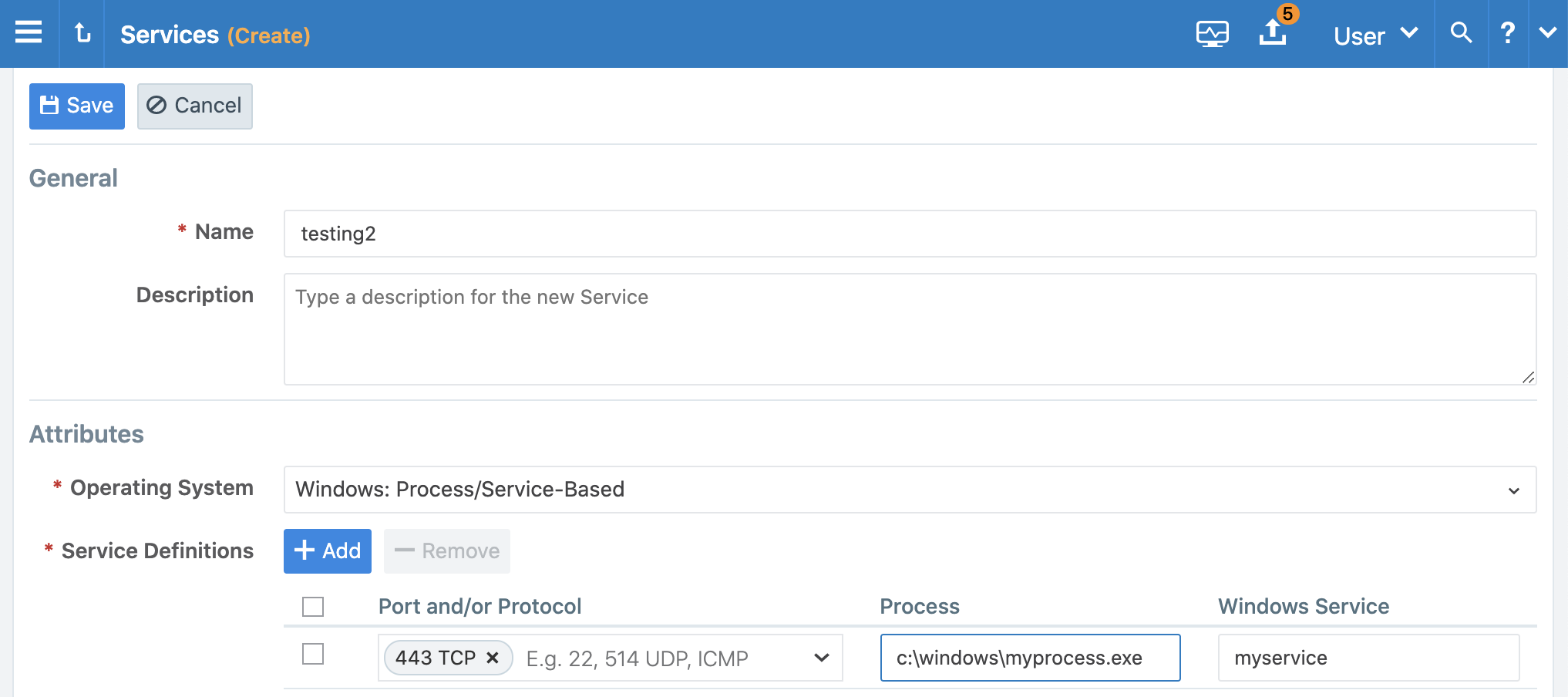
Enter the service a name and description (optional).
-
Under Attributes, choose whether you want to create a port-based or Windows service-based service.
-
In the Port and/or Protocol section, click Add and enter the ports, using a space to separate them from the protocol. If you want to enter a range, separate the port numbers by a hyphen. You can also copy and paste lists of services here from another source.
-
When the service uses any UDP ports, enter them as well.
-
Click Save.
To create a service from the Ruleset page:
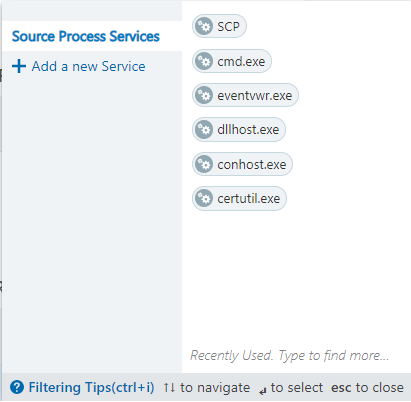
To make rule writing easier, you can create a new service in a ruleset as you are writing rules.
The service is not associated with the ruleset.
- Create a rule. (See Rules.)
-
In the ...Services field, choose Add a new Service at the end of the list.
-
Finish creating the service as you would when creating it from the Services page, described above.
Create a Service that features Windows Process-based Rules
Rules can be created specifically to allow all system-initiated processes in Windows. This approach allows all traffic related to drivers and other operating system modules. You can create a service of type Windows—process or service-based—with word “system” (case-insensitive) in the Port/Protocol text input field. Once you create this service, you can use it in rules.
To create a service that allows all system-initiated processes:
-
From the PCE web console main menu, choose Policy Objects > Services.
- Click Add.
- Enter a name and definition for the service you are adding.
- To add a service definition, from the Operating System drop-down, select either All Operating Systems:Port Based or Windows Process/Service-Based:
- If you select All Operating Systems: Port-Based, you can only indicate a port, a protocol, or both, separating the port and protocol with a space. For example, port
512 TCP. - If you select Windows Process/Service-Based, from the Port and/or Protocol drop-down, specify a port/protocol, a process or service, or a port/protocol with a process or service, separating the port and protocol with a space. For example, port
512 TCP, processC:\windows\myprocess.exe, and Windows service,myprocess.
- If you select All Operating Systems: Port-Based, you can only indicate a port, a protocol, or both, separating the port and protocol with a space. For example, port
- To remove a service definition, from the Operating System drop-down, select either All Operating Systems:Port Based or Windows Process/Service-Based:
- Click the check box next to the Port and/or Protocol. You may select a single or multiple entries.
- Click Remove.
- To add a service definition, from the Operating System drop-down, select either All Operating Systems:Port Based or Windows Process/Service-Based:
- Click Save.
Create a Service Using Windows Environmental Variables
The Windows environmental variable can be used to specify the full path. This can be done by creating a Service of type Windows: Process or Service based with the environment variables in the Port Protocol text input field
Currently, only the Windows System variable is supported for use in the process path. For example %systemroot%\myprocess.exe
Rules can be created to allow all system-initiated processes in Windows. This will allow all traffic related to drivers and other operating system modules. This can be done by placing the word system (case-insensitive) in the text input field.
To create a service that uses Windows environmental variables:
- From the PCE web console main menu, choose Policy Objects > Services.
- Click Add.
- In the Name field, enter
system(case-insensitive). - From the Operating System drop-down list, select Windows: Process/Service-based.
-
In Ports & Protocols, specify the port/protocol, separating the port and protocol with a space. For example:
%systemroot%\myprocess.exe - Click Save.
IGMP Services
IGMP can be added as a service and used in rules to write granular inbound or outbound policy for IGMP, which is typically used for multicast. No range is required for IGMP.
You can export IGMP traffic in JSON, CEF, or LEEF format.
Caveats
- When IGMP service is used in a rule, all IGMP types are allowed; however, granular control and specific multicast addresses are not supported.
- IGMP is not supported in the Illumination map.
ICMP Services
ICMP can be added as a service and used in rules to write granular inbound or outbound policy for ICMP. ICMP is usually used for traceroute and path MTU discovery.
You can export ICMP traffic in JSON, CEF, or LEEF format.
When these services are blocked, they do not appear in the Blocked Traffic list and the connection is dropped silently.
ICMP types/codes (such as 0 ICMP or 3/2 ICMP) are supported. The ICMP range is from 0 to 255.
The following table describes the correct format for each type of supported ICMP rule:
| Example | Format | Meaning in Rule |
|---|---|---|
| ICMP (on a new line) | Protocol name only | Allow all ICMP traffic |
| 3 ICMP | Protocol and code | All ICMP traffic is type 3 (Destination Unreachable) allowed, regardless of the code used in the rule |
| 3/6 ICMP | Protocol name, type, and code |
Only type 3 and code 6 ICMP traffic is allowed |
ICMP traffic is displayed in Explorer, similar to TCP/UDP traffic. You can see ICMP traffic flows in Illumination and the App Groups Map. You can choose to conceal them by using the filter in Illumination.
Caveats
- ICMP is not supported for virtual services.
- When an ICMP service is used in a rule, all ICMP types are allowed; however, granular control and specific multicast addresses are not supported.
-
When you enable IPv6 on Windows VENs, IPv6 systems rules are not propagated to those VENs. You need to write security rules to ensure robust IPv6 functionality. The ICMPv6 types that are required in those rules are as follows:
ICMPv6 Message ICMPv6 Type Router Solicitation Message 133 Router Advertisement Message 134 Neighbor Solicitation Message 135 Neighbor Advertisement Message 136
Filter the Services List
You can filter the Services list using the property filter at the top of the list. You can filter list by entering a service name, description, port, protocol, and provision status (draft or active).
Services in a Rule
When you create a rule, you can select a service to indicate the allowed communication between workloads and other entities. Every rule must have a destination service (port or process based), but having a source process or service is optional.
Services Caveats
Do not delete any of the objects (e.g., labels, rulesets, pairing profiles, or services) associated with an endpoint group. This will break the onboarding, pairing, etc., which may result in unexpected behavior.